
14 October 2024
Two first-year students at Stellenbosch University describe how they discovered bugs and fraud in SASSA’s SRD grant application system.
We are two first-year computer science students at Stellenbosch University. We have been looking for vulnerabilities in government as well as private-sector systems. We do this completely legally, by using publicly available internet resources, such as the backends of various government portals.
We inform all relevant institutions of any vulnerabilities we find, and in most cases give them sufficient time to address the issues before we disclose them publicly. We never exploit the vulnerabilities for our own benefit.
But sometimes a system bug is so bad that it brings to light fraud or gross incompetence. We believe it is right to then go public with what we find immediately. This is the case with SASSA’s Social Relief of Distress (SRD) grant system.
When we uncovered the problems described here, we did try to alert SASSA but found it near-impossible to get hold of anyone. Most of the contact numbers listed on their website either do not exist, or ring indefinitely.
Millions of people are receiving the SRD grant. Many have applied but their applications have been turned down. This grant, R370 per month currently, is touted as a possible forerunner to a basic income grant.
We queried SASSA’s public portal with 300,000 ID numbers for February 2005 at a rate of 700 per minute. The first problem is that this shouldn’t be possible. A competent system with basic security would have limited the rate at which we could query it.
We would have considered this a mere bug, informed SASSA and given them an opportunity to fix the problem before disclosing it. Except we discovered a bigger problem.
We found that 74,931 SRD grant applications were made for people born in February 2005. According to Statistics South Africa (as of 2020) there were 82,097 births in February 2005. This would mean that the application rate is roughly 91%. It is extremely unlikely that so many applications were made by people born in this month.
We also processed the first 500 male and 500 female IDs of people born on 1 January, from 1960 to 2006. Our findings show that there was an average application rate of 52% for all of the years, but when looking at people born between 2002 and 2006, the application rate becomes roughly 90%. This is notable because it reflects the application rate of people who have turned 18 since the grant was first issued in 2020. A 90% application rate is extremely unlikely to have occurred naturally - it is disproportionately large and reeks of fraud.
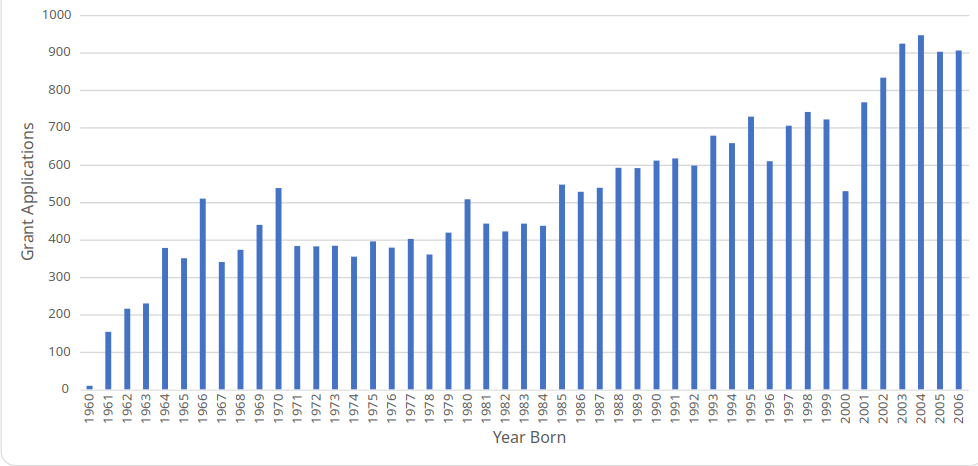
SASSA SRD grant applications for first 500 male and 500 female ID numbers on 1 January of each year from 1960 to 2006.
We also uncovered that SASSA has paid grants out on a number of occasions to applicants that used our ID numbers, even though we have never received the SRD grant. This suggests that not only are fraudulent applications being made; it is likely many of them are succeeding. Not only are ineligible people receiving the grant, but there are likely people who are eligible who are losing out because a fraudster is getting what should be their grant.
We conducted an on-campus survey of 60 people we know. 58 of them had active grant applications for the SRD grant on SASSA’s system. 56 of them stated that they had never actually applied for the grant themselves, which means that 56 are fraudulent applications.
The scale of this strongly points to an organised effort to take advantage of SASSA’s weak IT system. A question to ask is whether the system was intentionally implemented to be so weak. If not, then why has it taken SASSA so long to notice it? Why is it not properly fixed yet? And why has the public not been properly informed about what’s going on?
We went public with our findings on Thursday on Heart FM. Since then Brenton van Vrede, who heads up grant operations at SASSA, admitted, also on Heart FM, that fraud is widespread.
“We do unfortunately have quite a lot of these cases,” he said, which is quite an understatement.
Van Vrede asked people who discover that fraudulent applications have been made in their name to contact SASSA’s call centre, so that they can go through a biometric verification process. We are sceptical that this is practical. This is also a huge burden to place on members of the public, especially the poorest of the poor, to address a problem of SASSA’s making.
Unfortunately, the scale of this crisis means there is no easy solution to it. The entire SASSA SRD system needs to be re-envisioned. We recommend that SASSA not only reverify every single grant application, but that it also requests additional details to verify. Alternately it needs to reimplement the system from scratch, though this would be a huge undertaking that would likely leave many SRD recipients out of pocket.
SASSA’s commitment to biometric verification defeats the purpose of the SRD grant, which is supposed to be accessible, even to people using devices with the lowest specifications.
Instead, verification can include details such as the Smart ID issue date (found on the back of ID cards), which is what some banks and other institutions use. But more importantly, the system should be fixed so that it is harder to make applications in quick succession and impossible to commit fraud on a large scale.
SASSA needs to fully disclose what has happened and the scale of it. There needs to be an inquiry into what has happened. Who developed the SASSA SRD system? How much did it cost? Who maintains it? What security checks have been put in place? And who are the kingpins responsible for what is almost certainly an organised massive fraud?
GroundUp has been partnering with Heart FM on this story.